Note: GIAC reserves the appropriate to change the requirements for each certification unexpectedly. Based upon a scientific passing point review, the passing stage to the GMOB Test has long been identified to be seventy one% for all candidates receiving use of their certification attempts on or right after December 24th, 2016.
Watch out for applications that guarantee to monitor the activity of your family members and youngsters—Actually, They may be spyware that's “created to allow for very invasive electronic surveillance via a smartphone,” Pargman claims. Abusers can use these apps to examine texts and e-mails, keep track of the phone’s area, secretly listen to nearby conversations, and just take shots, amid other routines. Even a lot less insidious apps can even now collect data about Everything you do on your smartphone, Pargman claims.
I are not able to cite a source for discussions I've experienced / heard in real everyday living, but I comprehend your reasoning.
While these hackers tend not to share the destructive intent typically attributed to unauthorized hackers, they also don’t essentially adhere into a code of ethics like approved hackers.
Unless of course you browse the small print of the privacy policy or bother to scroll with the internet pages of the phrases-of-assistance statement, you have neither an indication that this data collecting is going on nor particulars concerning what data is currently being despatched to third events, but that transmitted data contributes to the profile of you that advertisers then use to target advertisements.
So, let us Examine the top seventeen mobile security experts who drastically affect the cybersecurity ecosystem and make it easier to keep forward in the game.
Adhere to the instructions under to reset your iPhone or Android. Guidelines for resetting an iPhone
@schroeder - yeah that is particularly my issue, we are only self-assured During this to the extent of "I would not Consider so"
A business mustn't kick out a tech person if he finds exploits in their platform. But Apple did! Apple fired Charlie for the reason that he discovered vulnerabilities during the App Keep. Charlie is amongst the most popular celeb With regards to mobile security. He is ex-Apple, ex-Twitter, ex-NSA and at the moment dealing with Uber. Not long ago, he and his fellow cybersecurity researcher Collin Mulliner claimed that each iPhone During this earth can be hijacked by sending 1 straightforward message.
After an attacker has utilized among the list of techniques outlined over to realize a foothold with a smartphone, what’s their next stage? While smartphone OSes are in the long run derived from Unix-like techniques, an attacker who’s managed to pressure a breach will see themselves in an extremely different atmosphere from the Computer system or server, suggests Callum Duncan, director at Sencode Cybersecurity.
Messenger, and Twitter. He has posted various white papers which you'll be able to perspective from best website his LinkedIn profile.[bctt tweet="I'm progressively worried about the current #security posture of the globe’s infrastructure @cesarcer" username="appknox"]
On iPhone, you are able to Examine which of your applications makes use of the digital camera or mic by going to the phone's Control Centre and examining the dots icon at the top.
While almost all of our unlocks only acquire quarter-hour, we give you complete updates which includes specifics of your checks, blacklist status, deal standing, plus more within the tracking location.
David could be the best particular person to get in touch with For anyone who is especially on the lookout for mobile phone market professional. He is the founder of copperhorse.co.British isles which supplies consultancy for mobile security and is very active on his website blog site.
 Tahj Mowry Then & Now!
Tahj Mowry Then & Now! Seth Green Then & Now!
Seth Green Then & Now! Hailie Jade Scott Mathers Then & Now!
Hailie Jade Scott Mathers Then & Now! Elin Nordegren Then & Now!
Elin Nordegren Then & Now!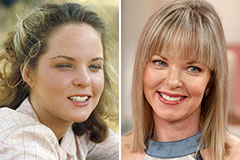 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!